SSH or Secure SHell is an encrypted connection protocol which is used to connect to the command line interface of a remote machine. Mac OS features a built-in SSH client called Terminal which allows you to quickly and easily connect to a server. In this article, we'll outline how to SSH to a server using the Terminal program on OS X Mac. OpenSSH is the premier connectivity tool for remote login with the SSH protocol. It encrypts all traffic to eliminate eavesdropping, connection hijacking, and other attacks. In addition, OpenSSH provides a large suite of secure tunneling capabilities, several authentication methods,.
Just for kicks, I wanted to try using an ECDSA key for ssh authentication. Unfortunately, the OpenSSH bundled with Mountain Lion (10.8) does not support ECDSA keys (nor can one even be generated with ssh-keygen.) The man pages for ssh-keygen and ssh-agent say they support ECDSA, but this is due to a naive man page generation assuming that since the OpenSSL library supports it, OpenSSH will too. Also, a PCI compliant OpenSSH isn’t bundled with OS X Lion (10.7) or older so this will also be useful for those users as well. Thankfully, Homebrew already has a recipe for installing an up-to-date OpenSSH so most of the work of upgrading is already done.
If you don’t already have Homebrew installed, follow its installation instructions first.
1. First we’ll need to add the system duplicates repository to Homebrew.

$ brew tap homebrew/dupes
2. Compile and install OpenSSH. I want to use a newer OpenSSL and all its optimizations, which Homebrew will happily provide via an option. Also, to make ssh-agent launchd and keychain compatible, there’s a nice undocumented option to apply the necessary patch before compiling too.
$ brew install openssh --with-brewed-openssl --with-keychain-support
3. Like the caveat notes when brew finishes, you need to update the launchd plist for ssh-agent to use the new Homebrew binary. By replacing /usr/bin/ssh-agent with /usr/local/bin/ssh-agent

$ launchctl stop org.openbsd.ssh-agent$ launchctl unload -w /System/Library/LaunchAgents/org.openbsd.ssh-agent.plist$ sudo vi /System/Library/LaunchAgents/org.openbsd.ssh-agent.plist$ launchctl load -w -S Aqua /System/Library/LaunchAgents/org.openbsd.ssh-agent.plist
4. The SSH_AUTH_SOCK env var needs to be updated for any open or new terminal sessions. It’s best to logout/login or restart because we cannot modify the variables in the user session scope that all new processes inherit from. However, if that’s not an option, can do this instead.
$ export SSH_AUTH_SOCK=$(launchctl getenv SSH_AUTH_SOCK)
5. Generate an ECDSA key
$ ssh-keygen -t ecdsa -b 521
Once the pub key from your new ECDSA key pair is added to .ssh/authorized_keys on your server(s), should be good to go (assuming OpenSSH on your server also supports ECDSA keys.)

Mac Ssh Manager
Here are openssl speed runs showing considerable improvements in the newer OpenSSL on a Late-2012 rMBP with a 2.9 Ghz i7 (Ivy Bridge):
If you want to setup SSH tunnel with your remote server using your Macbook, you can easily do so using the default Terminal application available in the Mac OS. Yes, we do not have to install any other application for doing so, like we do in Windows.
If you are a Windows user, I would recommend using Mobaxterm application for doing this.
What is SSH Tunneling?
An SSH tunnel or SSH port forwarding is a mechanism to establish a secure connection between a client machine and a server.
Let's take a simple example to understand this. If we have a database server, let's say MySQL running on a remote server with some IP address XXX.XXX.XXX.XXX and for which the port number 3306 which is the default port for MySQL is only available on the local network of the remote server. In this case, if you want to access the DB server from your local machine(connected to the internet), you won't be able to do it. In such a scenario, we set up an SSH tunnel with the remote server, to securely connect to the local network of the remote server to access the 3306 port on the remote server.
Let's take another example If we are using AWS service and we have two servers one is a DB server and another is the SSH server on which the Web Server is running. On the SSH server, because we are running the Web server, port 80 would be open to all, because then only the website or the web application hosted on that server will be available to its users. But, for security, the DB server is never exposed to the internet and is kept on the local network, which will be accessible via the SSH server, as the SSH server is on the same local network.
Now, if you want to check something or do something on the DB server. or want to connect your local SQL client with the remote database, you won't be able to do it directly. But because the DB server is accessible via the SSH server, we can setup an SSH tunnel with the SSH server to reach the DB server.
I hope the two examples are clear, and now you know, why SSH tunneling is needed. So let's see how we can do this.
Using MacOS/Ubuntu Terminal
We can use the ssh command to set up an SSH tunnel with a remote server, considering the SSH port which is port number 22 is open for the remote server.
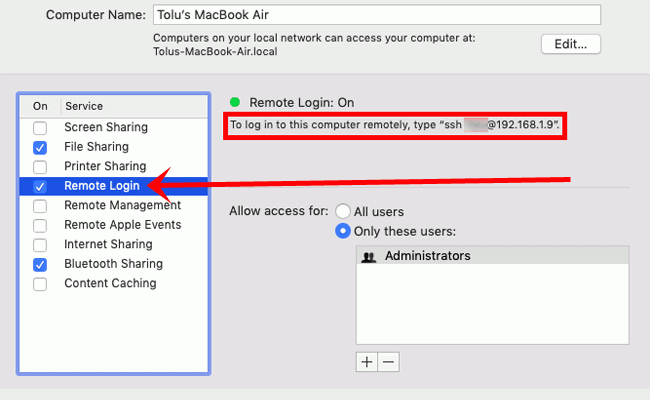
Install Openssh Mac
If our remote server name is my-remote-server.host and the SSH user is st-user, and on the same server a DB service let's say MySQL is installed which is accessible via localhost:3306 on the remote server.
Then to connect to the DB server, we can run the following command to setup an SSH tunnel:
Here,
8888: This is the local port that we will open for the SSH tunnel on the local machine. Here you can give any port number after 1024, because until 1024 port number, all ports are privilege ports.
127.0.0.1: This is the IP for the localhost running on the remote server, this is also the destination we aim to reach via the SSH server.
3306: This is the destination port, assigned to the MySQL sever on the remote SSH server.
and then [email protected] is the username and the IP address/URI for the SSH server.
Mac Os Ssh
Once you do this, you will be prompted to enter the password for the user st-user, so enter the password an hit Enter, and the SSH tunnel will be created. Now, you will be able to access the MySQL server using 127.0.0.1:8888 address from your local machine.
Using a .pem file
Ssh Client For Mac
If your remote server is an EC2 instance on AWS and you have a .pem file as the SSH key, run the following command for the above scenario:
In this case you will not be asked for the password, as authentication will be done using your SSH key.
This was the scenario where the DB server was running on the localhost of the remote server. Next, let's see how to connect to a separate DB server via a remote server.
Connect to Destination server via Remote Server:

If our DB server is my-db-server.host on which port 3306 is available for connection on the private network access to the remote SSH server my-remote-server.host, as shown in the picture below.
Then we can run the following command:
Note: If SSH connection is enabled on a different port other than the port number 22, then we can specify the port number in the above command using -p [PORT_NUMBER] argument. So, for example we have 2200 port for SSH enabled on our remote server, then the command would be:
Conclusion:
Openssh Server Mac
I hope this article helped you in understanding what SSH tunneling is and how we can setup an SSH tunnel using the Terminal in MacOS and in Ubuntu or other Linux based operating systems. If you were not able to do this or faced any issue running the above command do share in the comments below and we will help you out.
