- Azure Sophos Xg Pricing
- Azure Sentinel Sophos
- Sophos Xg Admin Guide
- Sophos Xg Firewall Pricing
- Azure Sophos Xg Firewall
With version 18 Sophos brings changes to RADIUS settings on XG Firewall. We now have possibility to set timeout for authentication and this allows us to use Azure MFA for 2-factor authentication.

Here is few simple steps how to enable this on network policy server and on XG Firewall.
Azure Sophos Xg Pricing
Azure Firewall is rated 7.4, while Sophos XG is rated 8.0. The top reviewer of Azure Firewall writes 'Easy to set up, good integration, and the technical support is good'. On the other hand, the top reviewer of Sophos XG writes 'Light and stable with excellent real-time control '. Azure Firewall is rated 7.4, while Sophos XG is rated 8.0. The top reviewer of Azure Firewall writes 'Easy to set up, good integration, and the technical support is good'. On the other hand, the top reviewer of Sophos XG writes 'Light and stable with excellent real-time control '.
If you do not have MFA enabled for your Office 365/Azure AD account you can enable it trough following link https://aka.ms/mfasetup or use conditional access policy to enforce MFA for user accounts.
Only push message trough Microsoft Authenticator App or phone call can be used for 2-factor authentication with SSL VPN/Sophos Connect. To prevent users for selecting any other possible multi-factor authentication method you should disable verification options that are not supported.
To enable or disable verification methods, complete the following steps:
Azure Sentinel Sophos
- In the Azure portal, select Azure Active Directory, then select Users.
- Select Multi-Factor Authentication.
- From Multi-Factor Authentication, select service settings.
- Unselect Text message to phone and Verification code from mobile app or hardware token
- Click Save.
Azure AD Premium P1 license should be enabled on all users using Azure MFA trough RADIUS extension. For more information refer to https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-mfa-licensing
Also remind that Network policy server with Azure MFA extension redirects all requests to Azure. Server cannot be used for any other kind of authentication (I.e. 802.1x) after enabling extension.

1. Install Network Policy Server role on Windows server. I installed mine on my LAB Domain Controllers.
2. Install Azure MFA extension and configure it. Follow guide from Microsoft to enable it.
Download:
https://www.microsoft.com/en-us/download/details.aspx?id=54688
Guide:
https://docs.microsoft.com/bs-latn-ba/azure/active-directory/authentication/howto-mfa-nps-extension

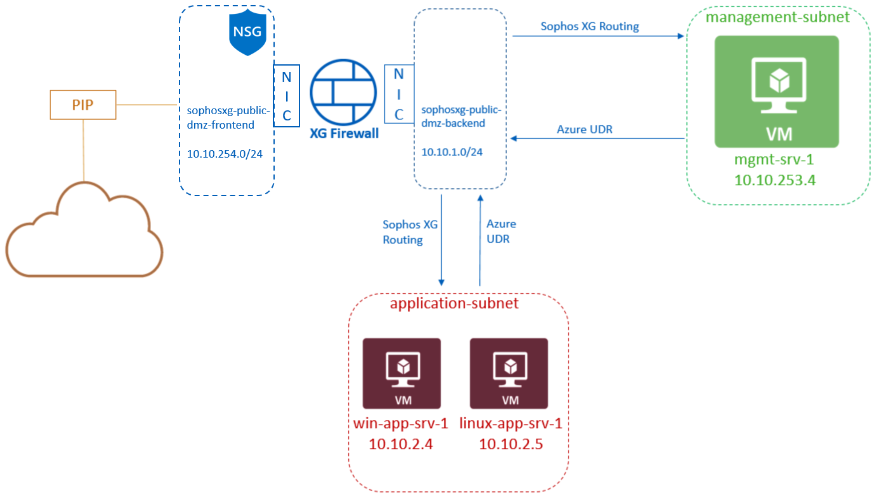
3. Create new RADIUS client with IP address of the Sophos XG Firewall.
4. Create new Connection request policy.
5. Create new Network Policy
Sophos Xg Admin Guide
6. Create firewall rule on RADIUS Server to allow connections from Firewall.
Sophos Xg Firewall Pricing
7. Add authentication server in Sophos XG Firewall.
8. Test authentication trough RADIUS.
Azure Sophos Xg Firewall
9. Select where you want to use RADIUS as authentication back-end.

